There are a lot of pitfalls when you want to deploy or update to VMware vSphere 5.1. Beside the vSphere Web Client, the most discussed new component is the new authentication engine called Single Sign On (SSO) which is mandatory for the vCenter Server. I've already written about a simple deployment scenario where a vCenter Server (Appliance or Installable) can be authenticated against a single Active Directory domain. In this post i am going to explain the changes and straits when using multiple trusted Active Directory Domains.
Common VMware Authentication Design
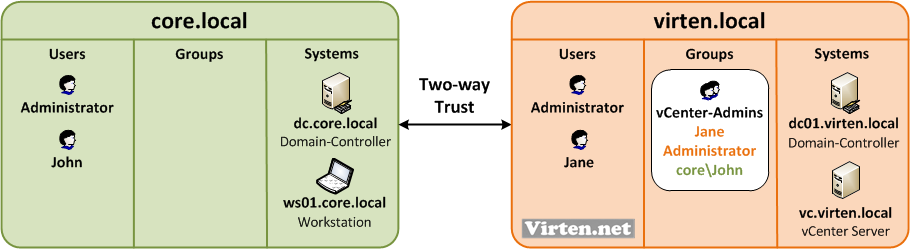
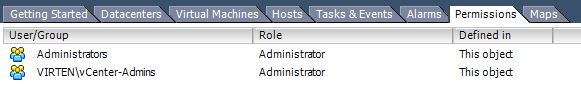
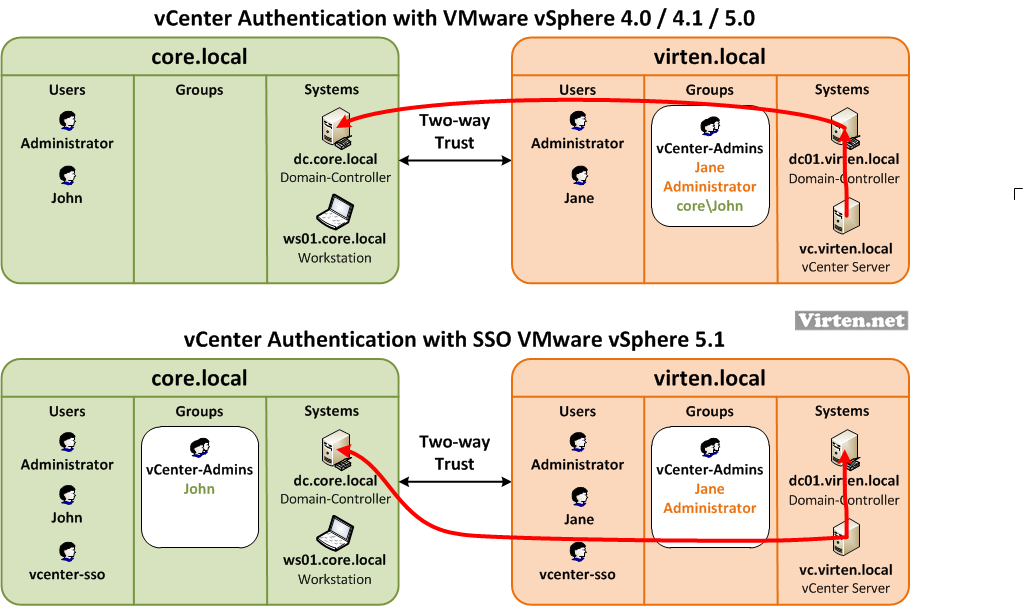
In my design example i have a core domain where all users are centrally managed. All administrator workstations also belong to the domain core.local. The customer has it's own domain called virten.local where the vCenter is located at. Both domains have a Two-way trust configured. To have a clear user management you would usually create a vCenter-Admins group at the virten.local domain and assign users from both domains to that group. This group is used to assign vCenter Server permissions. Until vSphere 5.0 the local windows operating system authentication was used for the vCenter Server, so this scenario worked without any flaws.
vSphere 5.1 Authentication Design
With vSphere 5.1 the authentication has been changed to a new service called Single-Sign-On (SSO). The local operation system is not longer used to authenticate against Active Directory. That means the following changes:
- Creating local groups with domain users to set permissions does not work
- Active Directory groups with users from other domains does not work
- All Active Directory Controllers have to be explicitly added to vCenter SSO
- A SSO-User with read permission is required in each domain
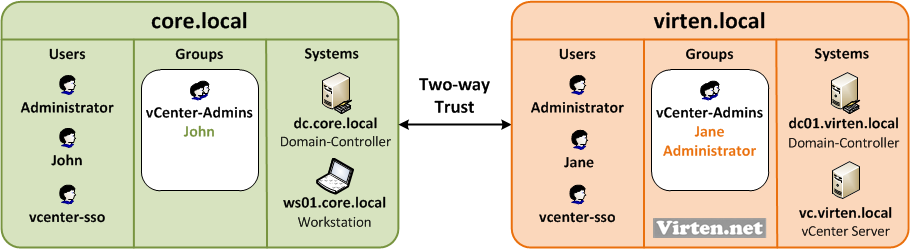
With that in mind, the logical authentication design has been changed. You have to create a vCenter-Admins group in each domain. You also need a vcenter-sso user and configure vCenter SSO for each domain:
Howto configure vCenter SSO authentication with multiple domains
- Create a group for vCenter-User in both domains
- Create a vcenter-sso system user for SSO configuration
- Add users you want to give vCenter permisions to the appropriate domain
- Add both domains as a identity source (Howto)
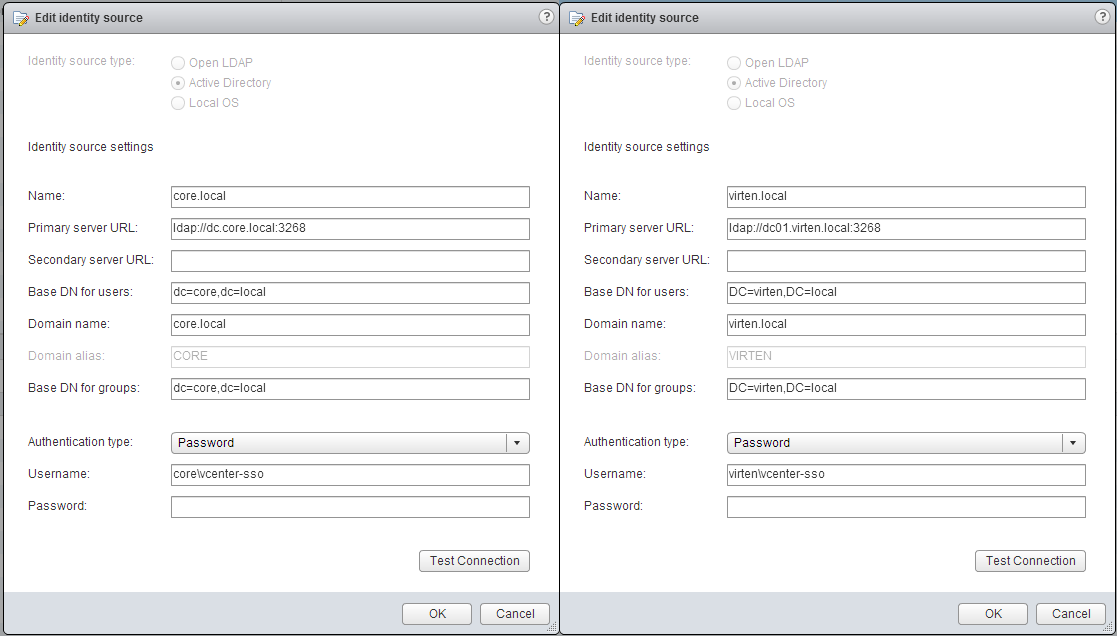
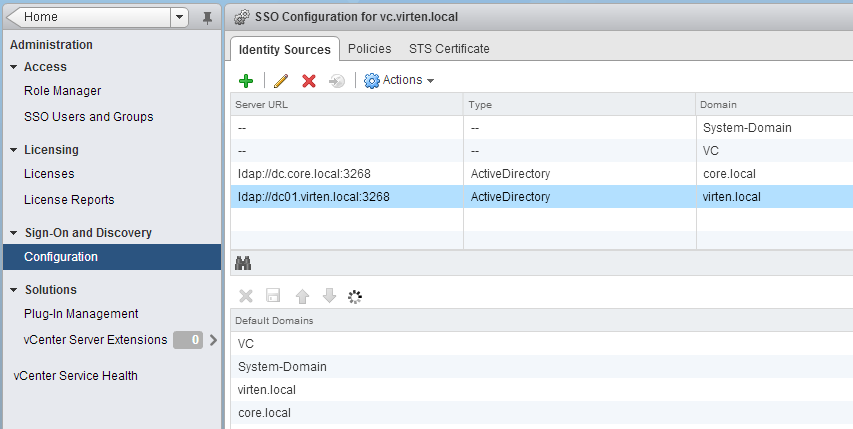
- Add both identity sources to Default Domains (Save!)
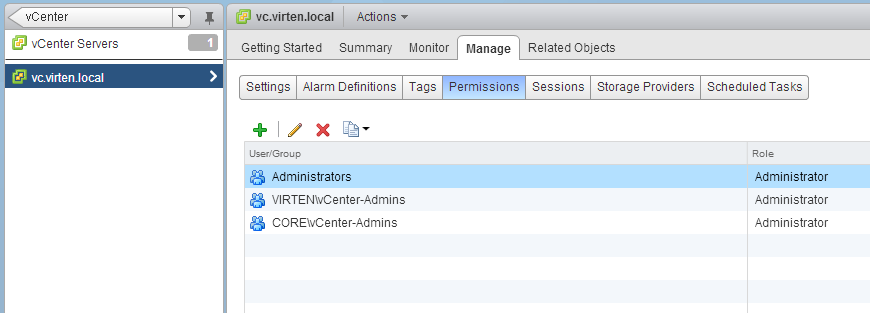
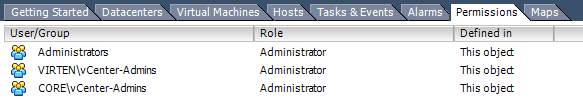
- Assign permissions to groups in both domains
- Done!
Use Windows session credentials/authentication
Does it work? Yes! If both domains are trusted, you can log in without entering a password. This works wherever the user comes from, unless it is allowed to log n and the Active Directory domains have a trust.
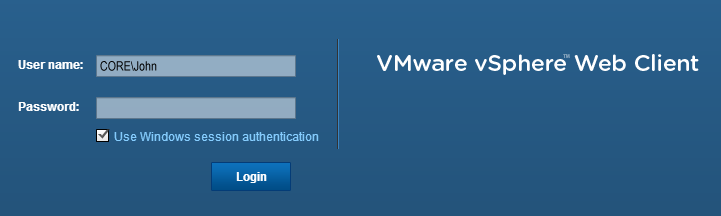
(Actually you do not need a trust between both active directories to make authentication work. You only need the trust to enable the usage of security tokes to login without passwords.)
Pingback: Howto: SSO – Simple AD Authentication with VMware 5.1 | Virten.net