With vSphere 5.1 a new component called Single-Sign-On (SSO) has been introduced. The new SSO service is mandatory since 5.1. There is no way around, you have to use it. The good thing about it is that it has various authentication options and can be deployed in an redundant fashion. Unfortunately it adds a lot of complexity to your configuration but if you understand all of it's components and functions, you won't miss it.
The simplest active directory deployment works with both, the vCenter Server Appliance and a vCenter installed inside windows. This method allows you to manage users and groups in your central directory. I will concentrate on VCSA for that post because this is the only possible deployment scenario for that appliance. If you have a more complex deployment with Active Directories in trusted states check this littele howto: Howto: vSphere 5.1 SSO with trusted Active Directory
Please note: The Use Windows session credentials / Use Windows session authentication checkbox does not work with this method as it requires kerberos which is provided by the RSA SSPI service. This service is not available when you are using VCSA. To make this button work in windows your vCenter Server has to belong to the domain you want to authenticate against.
- Open vSphere Web Client (https://<ADDRESS>:9443/vsphere-client)
- Login as root (VCSA) or admin@system-domain (Windows)
- Navigate to Administration > Sign-On and Discovery > Configuration
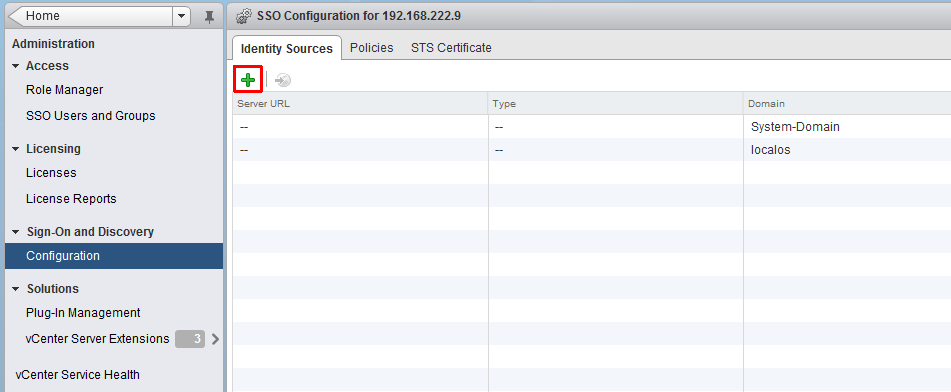
- (If there is no Configuration entry you are probably not logged in as admin@system-domain)
- Click the green + sign to add an identity source
- Select Active Directory
- Fill out the form, replace with your domain settings
- Name: virten (This is just a nunfunctional label)
- Primary server URL: ldap://dc01.virten.local:3268 or ldap://dc01.virten.local
Note: Port 3268 is the global catalog. Browsing the directory is much faster when asking the global catalog. - Secondary server URL: ldap://dc02.virten.local:3268 or ldap://dc02.virten.local(optional)
- Domain name: virten.local
- Domain alias: virten
- Authentication type: Password
Note: Anonymous or Reuse Session will not work with this method - Enter Username and Password (Can be a read-only user. I usually use an own sso user)
Note: You do not have to enter Base DN for users or Base DN for groups. It will use the directory root automatically. (You can modify that later if you want)
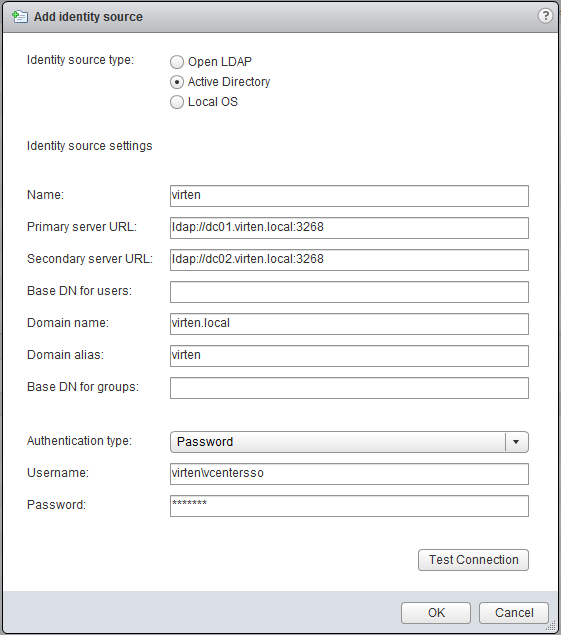
- Click Test Connection
It should tell "The connection has been established successfully."
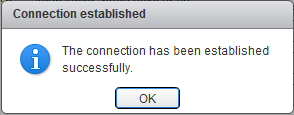
- Click OK twice
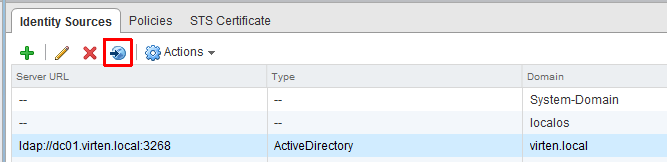
Back at the Identity Source Window your AD should appear in the list and from now on you are able to assign vCenter permissions to users or groups from your active directory (As you know from vSphere 5.0 and previous). But users can't login unless you add the identity source to the default domains. - Click the "world with arrow" button
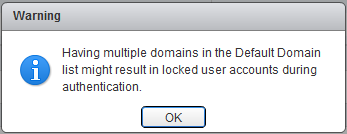
You should get an warning telling you that "Having multiple domains in the Default Domain list might result in locked user accounts during authentication". That means when you have the same username with different passwords in different domains (Mostly the Administrator user in Windows) you might authenticate against the wrong directory and lock account.
You AD should now appear in the bottom list. - Save the configuration
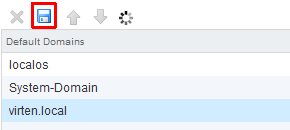
- That's it. You can now set permissions and authenticate against active directory with vCenter Server 5.1 though SSO.
Additional Hint: You might have noticed that you can move the default authentication source up and down. What is the best option? Where to put the active directory?
- The safest position for the AD authentication is the last place. This makes it unlikely that you accidently lockout yourself.
- If you want to authenticate without having to enter your domain (user rather than domain\user at the login-screen) you should place it on the first position to make the login process faster.
Always remember to hit save after changing sso configuration!
Common Issues
Cloud not retrieve Base DN for Users/Groups
You sometimes get an error message stating that it could not retrieve the Base DN. If you get this message, you have to enter the DN by yourself. The DN for both, users and groups for the domain virten.local is dc=virten,dc=local
![]()
Error 29148.STS configuration error
You got this error message when you try to use a specific named user for running the vCenter SSO service. Try to use the default (Local network account) instead.
Pingback: Howto: vSphere 5.1 SSO with trusted Active Directory | Virten.net
Thank you, this is the best write-up due to the #13's "Note" and "Additional hints" at the bottom.
Finally an article to explain this as it should be explains.
Thank you Thank you Thank you.
For those whom their lab is not onnected to the internet, just use this offline Adobe Flash installer:
http://forums.adobe.com/thread/1188659
Pingback: Howto: AD Authentication in vCenter SSO 5.5 | Virten.net