When you open a Support Request (SR) at VMware, the Global Support Services usually requests you to collect diagnostic information. You can create this log bundle with a special command line tool (vm-support), with the vSphere (Web-)Client or with the API. No matter how you create the bundle the result is always the same: a .tgz file containing your ESXi Host name and the creation date with a size of about 30 - 300MB.
This post explains what's inside this log bundle, but instead of simply extracting the file and looking at the result, I am going to take a look on how the file is created and what's part of the process.
Why is it important to know? Because it does not only contain data that allows VMware GSS to identify your issue, but also to help yourself to enhance your troubleshooting skills. The script gathers the output of many useful commands and there is nearly no black magic involved. You do not need special tools or internal VMware knowledge to make use of this log bundle.
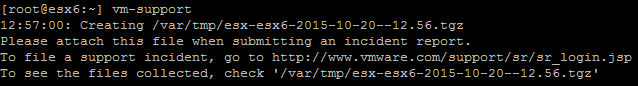
Read More »What's Inside an ESXi vm-support Bundle?