With the recently released VMware vSphere 5.5, the component Single-Sign-On (SSO) has been completely rewritten. The biggest change is that the RSA database has been removed, which eliminates much of its complexity. There is also a new identity type (Active Directory (Integrated Windows Authentication)) that works without specifying the AD Controllers directly, like the old vSphere 4.x / 5.0 authentication. The whole process is much easier. This post shows how to enable Active Directory Authentication within the new vSphere 5.5 Single-Sign-On. If you are using vSphere 5.1, read this post.
The method shown in this post allows you to manage users and groups in your central directory. This works for both, the vCenter Server 5.5 installed on Windows Server and the vCenter Server Appliance (VCSA).
- Open vSphere Web Client (https://<ADDRESS>:9443/vsphere-client)
- Login as administrator@vsphere.local
Password (Windows): Set during installation
Password (VCSA): "vmware" - Navigate to Administration > Single Sign-On > Configuration
-
- (If there is no Single Sign-On configuration you are probably not logged in as administrator@vsphere.local)
- Click the green + sign to add an identity source
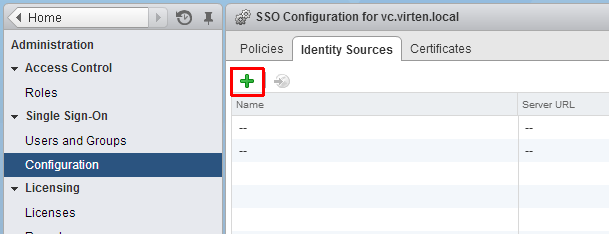
- Select Identity Source Type:
A) Windows based vCenter Server 5.5:
Active Directory (Integrated Windows Authentication)
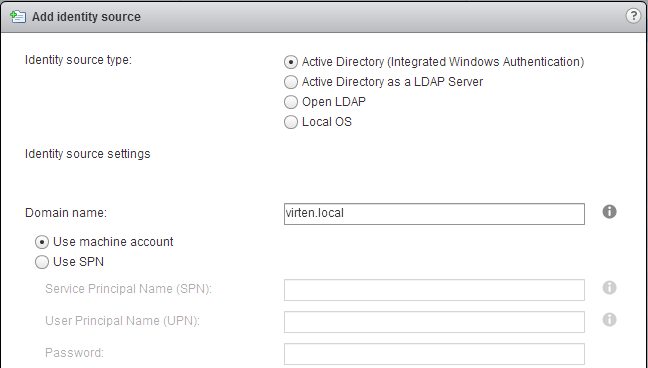 B) vCenter Server Appliance 5.5 (VCSA):
B) vCenter Server Appliance 5.5 (VCSA): -
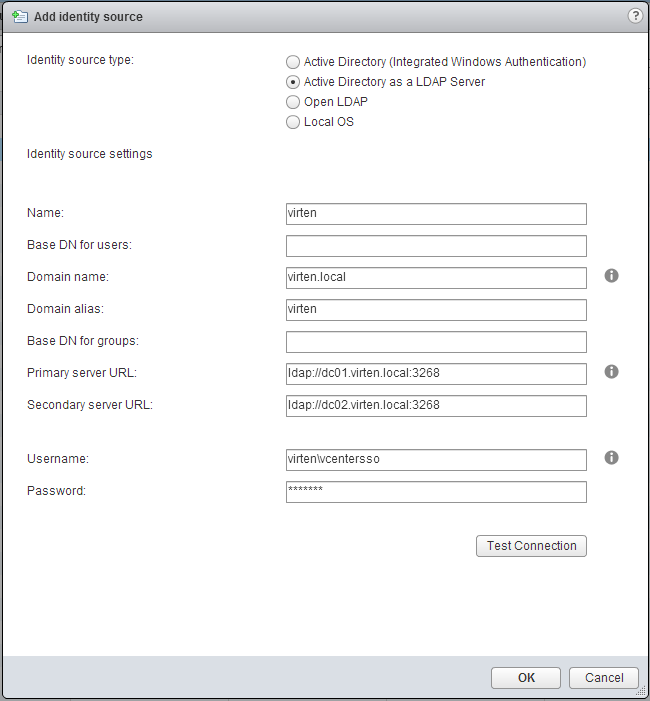
- Click OK
- Back at Identity Sources your AD should appear in the list and from now on you are able to assign vCenter permissions to users and groups from your active directory. When you are using the Integrated Windows Authentication, trusted domains are also available. The functionality is very similar to vSphere 4.x and vSphere 5.0
- Select you Active Directory and click the "world with arrow" button to make AD to your default domain.
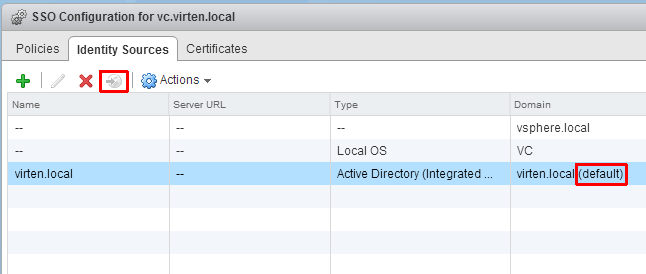
- You should get an warning telling you that "This will alter your current default domain. Do you want to proceed?". This is okay, as you can only have one default domain.
- That's it. You can now set permissions and authenticate against active directory with vCenter Server 5.5 though SSO.
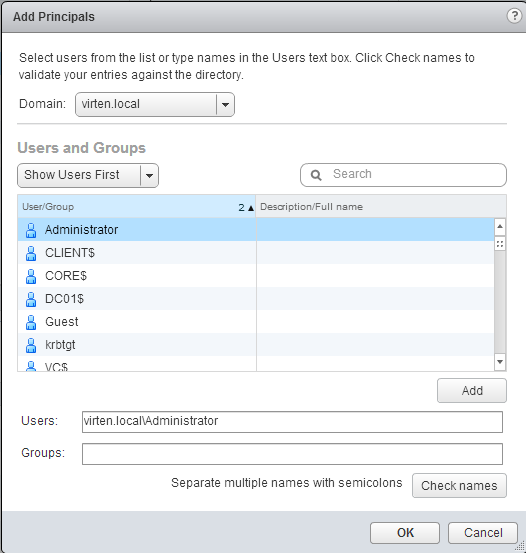
To change the vCenter Server SSO configuration with other users than administrator@vsphere.local, you have to add them to the Administrator Group within SSO:

Great summary. I just installed a new 5.5 environment and it was so much easier than the 5.1 installation! I was wondering where it put the RSA database. Glad I don't have to worry about that anymore!
Thanks a ton mate; this made my deployment a hell of a lot faster. Cheers!
Pingback: Devilsystems.org » Blog Archiv » vSphere 5.5 und Active-Directory Authentifikation
Very nice:)
This guide is missing one thing which are the permissions in the Virtual Center level(through the Web Client).
Only then you'll be able to log in with the domain user
Bingo.
:)
Thanks for your comment. I was struggling with the exact problem. Eureka!!
Good stuff. But, I wonder why you don't just join the vCSA appliance to the domain by enabling AD on the Authentication tab at the port 5480 URL? Then you can use the Integrated Windows Authentication as you do for a Windows-hosted vCenter Server -- works well for me! The "AD as LDAP Server" solution suggested here appears both clunky, and limited.
Exactly! Windows as LDAP is indeed clunky and a poor approach. If you're adding AD authentication, simply make sure the VCSA is added to the domain, then use Integrated Windows Authentication using the computer account. Couldn't be simpler.
Thanks,… this was a clear, concise and complete explanation.
- h
Hi I have vcenter 5.5 installed with heartbeat enabled between two VC's. Though all is good and installed and HB is good i am experiencing occasional " tranport error connection" when i log into the vcenter and also when i do the weblogon and fat client log it fails and connects and fails etc its being sporadic - Any inputs - Thanks
Try to disable firewall/antivirus solutions and see if the problem persists. Have seen similar problems caused by antivirus software.
Pingback: Top 10 Posts of 2013 | Virten.net
Hi,
I was wondering if with SSO alone is enough to work, i mean, without including AD. Would it be possible for example to centralize everything in SSO (ESX credentials and other vsphere components crendentials) without adding AD ? For example, you want to change the root account for all the ESXs...
Thanks!
SSO is for central authentication. It can not change the root account for ESXi hosts.
Hello,
Thank you for this great article... Trying to do the same.
However despite I do have a successfull test connection, the interface prevent me to click "ok" before I fill in "base dn for users" and "base dn for groups" fields.
Some tips to figure out how to find out what they want and in what format (I'm not a ldap expert)
Thanks !
If you want to scan the entire AD named "company.local", your Base DN is
DC=company,DC=local
To generate more a complex DN, you can use this tool by Microsoft: http://technet.microsoft.com/en-us/sysinternals/bb963907.aspx
Thanks fgrehl !
In the meantime I did find the solution.
Now my appliance is connected to my DC
I did grant administrator and user role to a user of my AD.
When trying to login ... It just don't work...
from ssh console of VC appliance I can resolve and ping both DC
the system is not very "verbose" so hard to me to find out what is wrong... (servers are normally syncrhonized on UTC)
Any advice ?
Thanks !
Thank you! Very helpful. Couldn´t find this point at all in pubs.vmware.com
HI, is it possible to change the length of time it takes for the Web Client to poll AD for Group membership changes?
Thanks
despite doing all these we still get incorrect password
This was extremely helpful. Thank you very much!