Shell access to an ESXi host provides essential maintenance, configuration and troubleshooting commands. It can be used in cases that cannot be handled through the standard vSphere Client. In my case, I tend to have SSH activated by default. From a security perspective it is recommended to keep SSH disabled, but with the management network behind a firewall I feel secure.
If you are using SSH daily I am sure that you are familiar with the public key authentication. PKI is an authentication method that relies on a generated public/private keypair and enables the login without entering a password. This method is faster and more secure than entering a password manually because every administrator can have his own public/private keypair.
This post explains the methods how to enable and automate public key authentication with ESXi Hosts.
If you do not already have an SSH Key, the first step is to create an SSH Keypair:
Creating an SSH Keypair with Linux
It's a standard task to create a keypair with Linux. The public key you need to put on your ESXi host is stored in ~/.ssh/id_rsa.pub:
~ # ssh-keygen -t rsa -b 4096 Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: 99:b2:38:a0:47:1d:16:89:e5:e9:35:1c:cb:ac:1e:15 The key's randomart image is: +--[ RSA 4096]----+ | oo.E | | ...* + | | = O | | + = . o | | o = . S | | o o o o | |. . + . | | . . | | | +-----------------+ ~ # cat ~/.ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1y[...]
Creating an SSH Keypair with Windows
You need the following tools:
- PuTTY (SSH Client)
- PuTTYgen (SSH Key Generator)
- Pagent (SSH Auithentication Agent)
All programs are free and available for download here.
1. Open PuTTYgen
2. Click "Generate"
3. Move the mouse to generate random data. The result should look like this:
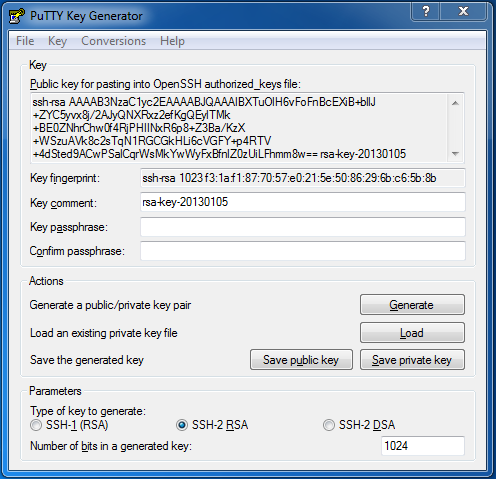
4. Click "Save public key" and choose a path
5. Click "Save private key" and choose a path. If you want to use this key for production you should set a passphrase at this point!
Enable the SSH authenticatien Agent
1. Start Pagent
2. Doubleclick the Pagent Trayicon
3. Click "Add Key" and open your private key file (.ppk)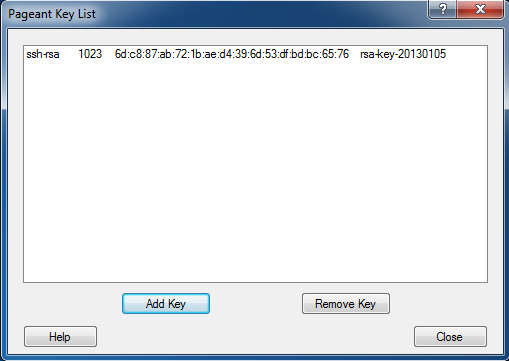
Deploy public keys
You public key has to be stored in /etc/ssh/keys-root/authorized_keys at the ESXi host. The file works the same way as the authorized_keys file on an Linux host. Do not use the ssh-copy-id command to copy your public key to another system. This does not work for an ESXi host.
1. Connect to the ESXi host using PuTTY
2. Login as root
3. You should be familiar with vi to edit the keyfile:
~ # vi /etc/ssh/keys-root/authorized_keys
4. Press i to enter "Insert Mode"
5. Copy your public key (one line, starting with ssh-rsa) and paste it into vi (right click)
6. Press <ESC> :wq <ENTER> to save and quit vi
Deploy public keys with Host Profiles
SSH Keys are part of Host Profiles. If the key is deployed on the reference host, it will be applied to all host within the host profile. If you want to edit the profile manually, you can found the configuration in:
Security configuration > SSH authorized key for root user > SSH public key for root user > Key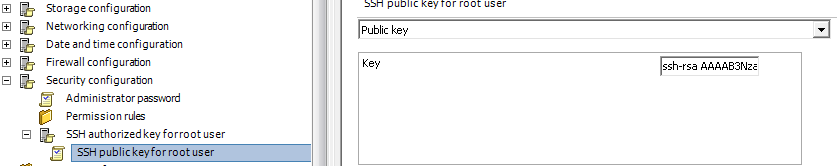
Deploy public keys during the installation with kickstart
You can add this snippet to your Kickstart configuration to automatically enable SSH, remove the Shell Warning and add your SSH Key to the ESXi host:
#esx/ssh vim-cmd hostsvc/enable_ssh vim-cmd hostsvc/start_ssh esxcli system settings advanced set -o /UserVars/SuppressShellWarning -i 1 cat > /etc/ssh/keys-root/authorized_keys <<EOF ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAgEAtuq[...] EOF #esxi/ssh end
sshAutoConnect Plugin
If you are using SSH, you should also check the sshAutoConnect Plugin made by vmdude. This Plugin allows you to connect to an ESXi host directly from the vSphere Client.
Nice post, hadn't used keys to authenticate against ESXi hosts before, but set it up this morning and works fine. Thanks
So, Something to mention is that the /etc/ssh/keys-root/authorized_keys is really only for the root user. If you want to use individual accounts then what?
you can create a new user with the web interface and assign it a role. from there, you just need to do this:
user=administrator # put whatever you need
dir=/etc/ssh/keys-${user}
keyfile=${dir}/authorized_keys
mkdir ${dir}
chmod +t ${dir}
touch ${keyfile} # create a blank file
chown -R ${user} ${dir} # make sure
chmod 0600 ${keyfile}
from there, you can add the public key in /etc/ssh/keys-${user}/authorized_keys
I just got this working for an ESXi user named 'betty'. Now I can `ssh` into my ESXi host as "betty" using a certificate instead of a password, which is great for running automated scripts that connect to the host. Here's what I did:
# Copy betty's SSH public key(s) onto the host
% mkdir /etc/ssh/keys-betty
% cat "...pub key here..." > /etc/ssh/keys-betty/authorized_keys
% chmod 600 /etc/ssh/keys-betty/authorized_keys
% chown -R betty /etc/ssh/keys-betty
# Test: make sure you can `ssh` into the host as *betty* using public
# key authentication
# Create a temp directory
% mkdir /tmp/myhost
% cd /tmp/myhost
# Create a .profile file (optional)
% cat > .profile
^D
% mkdir -p etc/ssh
% cp -pr /etc/ssh/keys-betty etc/ssh
# Create a compressed tar file in /bootbank containing .profile (if
# desired) and the etc/ssh/keys-betty/authorized_keys file
% tar czf /bootbank/myhost.tgz .profile etc
# Append myhost.tgz to the end of the "modules=" line in
# /bootbank/boot.cfg.
% vi /bootbank/boot.cfg
modules=b.b00 --- ... --- state.tgz --- myhost.tgz
Finally, add the following to /etc/rc.local.d/local.sh as the ownership specified in the tar file isn't honored when the files are unpacked:
# Enable SSH keys
chown -R betty /etc/ssh/keys-betty
Reboot your host and you should be good to go.
Ok, so I can now login as 'admin' to my host with a SSH key, but that broke the compliance to the Host Profile. Piece of cake to fix, added a user with the expected public key and the expected password to the Host Profile, it works... until I need to have a second key in authorized_keys. No way I can put more than one line in the vCenter interface.
Would you have an idea if it's even possible to store more than one public key in a Host Profile (it's possible the DB schema won't like that too much...)? Is it worth editing the XML profile? What do you think?
You can have multiple keys per user with host profiles. It's a single line in the host profile config but if copy a multiline text file to the field, it will work.