Platform Service Controller is a new component in vSphere 6.0. The PSC contains all the services that vCenter needs for its functions including Single Sign-On (SSO). This post describes how to configure AD authentication in vCenter Server 6.0.
The method shown in this post allows you to manage users and groups in your central directory. This works for both, the vCenter Server 6.0 installed on Windows Server and the vCenter Server Appliance (VCSA).
- Open vSphere Web Client (https://[vcenter]/vsphere-client)
- Login as Single Sign-On Administrator (Password set during installation)
- Navigate to Administration > Single Sign-On > Configuration
- Open the Identity Sources tab
- Click the green + to add an identity source
- Select Identity Source Type:
A) Active Directory (Integrated Windows Authentication)
This option works with both, Windows-based vCenter Server and vCenter Server Appliance. The underlying system (Windows Server or Infrastructure node of Platform Services Controller) has to be a member of the Active Directory domain.
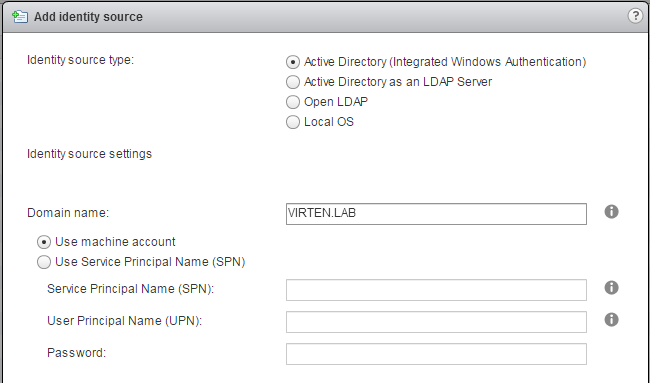 B) Active Directory as a LDAP Server
B) Active Directory as a LDAP Server
If the underlying system is not part of the Active Directory domain.Fill out the remaining fields as follows:
Name: Label for identification
Base DN for users: The Distinguished Name (DN) of the starting point for directory server searches. Example: If your domain name is virten.lab the DN for the entire directory is "DC=virten,DC=lab".
Domain name: Your domain name. Example: "virten.lab"
Domain alias: Your netbios name. Example: "virten"
Base DN for groups: The Distinguished Name (DN) of the starting point for directory server searches.
Primary server URL: AD Server URL. You can either query the local directory (Port 389), or the global catalog (Port 3268). Example: "ldap://dc01.virten.lab:3268"
Secondary Server URL
Username: A user in the AD Domain with at least browse privileges. Example virten\vcentersso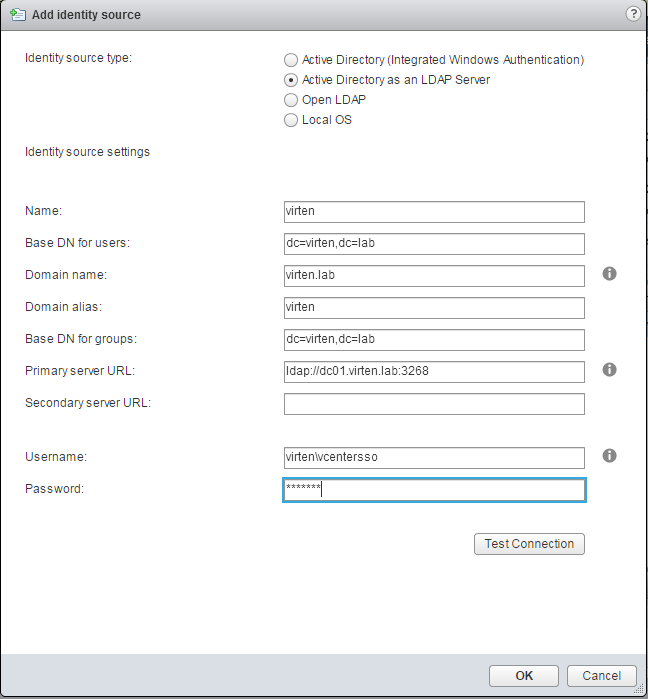
Press Test Connection to verify AD connection
- Click OK
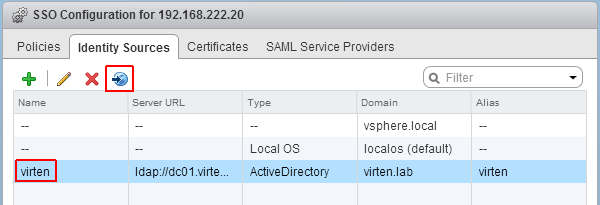
- Back at Identity Sources your AD should appear in the list and from now on you are able to assign vCenter permissions to users and groups from your active directory.
- Select you Active Directory and click the world with arrow button to make AD to your default domain.
- To login with AD users, you have to set permissions. To add a AD user as global Administrator navigate to Administration > Access Control > Global Permissions
- Click Add permission
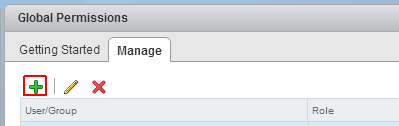
- Click Add...
- Select the Active Directory domain under Domain, choose a user and press Add
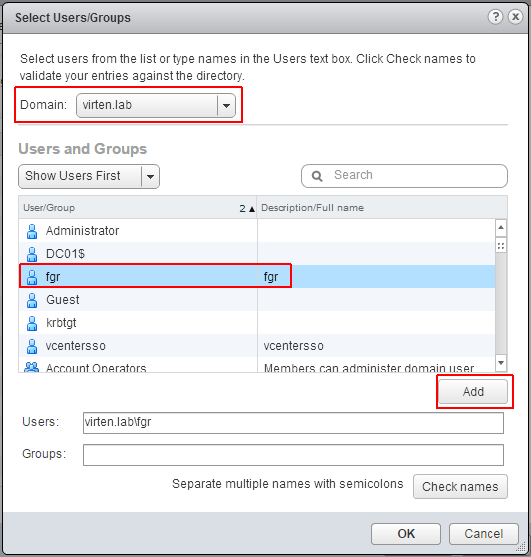
- Press OK twice
You can now login to the vSphere 6.0 vCenter with your Active Directory Account.
Pingback: vCenter Server Appliance 6.0 (vCSA) How to Join AD Domain | Virten.net
Pingback: How to get “Use Windows session” Checkbox to work in VCSA6 | Virten.net
Thanks for article.
Has anyone else had trouble joining vcenter 6 to a domain? I have followed every guide possible but not matter what it says my domain name is incorrect, which obviously it's not since I have done this 100 times before back in 5.5, 5 etc
What I've notice is that once you "join" there is no indication that you actually joined a domain until you reboot. If you don't get an error, chance are you have joined. It seems to be a bit of a bug in the interface that I can see. So confirm that. (can always check in AD to see if it's in there.)
That bit me a few times in the lab, but I haven't seen any indication of a problem anyone has mentioned.
Greg, Windows Firewall is the issue. Open up LDAP and other ports for this (or disable if you're like me in a lab)
Pingback: How to get “Use Windows session” Checkbox to work in VCSA6 | Sysadmins Technologies
Pingback: Integrating Platform Services Controller/vCSA 6.0 with Active Directory using CLI | Virtual Brakeman
Hi, I am running vCenter 6.0. After SSO configuration and adding the domain, I am not able to load users or groups from my domain. I can see the vCenter appliance is communicating with the DC. Do you know what ports we need to have open for pulling the AD groups?
Also I am not able to delete my domain and add it again. Even after a reboot. Do you know which config file holds the domain information and if it can be deleted? Thanks for your help
Hi,
depending on your configuration, Active Directory requires different ports. Typically you should open 389+636(LDAP), 3268+3269 (Global Catalog), 53 (DNS), 88 (Kerberos), 138 (Netbios) and 135 (RPC). For AD, DNS is very important. If it does not work properly you are facing issues...Not sure if that's your problem, but I've seen similar problems where DNS/Naming caused the issues.
If you can't join or leave the domain with the GUI, try to use the CLI Tool. Login with SSH and run /opt/likewise/bin/domainjoin-cli (The command has a good help page).
I've never tried to debug config files on the VCSA. Maybe in /etc/krb5.conf?
You should also check the SSO logfile, which gives very self-explaining error messages. (/var/log/vmware/sso/)
Hello fgrehl - Can you please tell me how to perform the DNS for AD, and how this can be done in a workgroup environment? I have client that is currently in a workgroup ( 150+ Desktops ) and I have a fresh 40 User 6.0 ESXI that I need to migrate some users to the other hosts that are 5.5 or 5.1. Please Advise - :)
Not sure if I understand your question. You can't use AD authenthication when you are only working with a workgroup. You need a identity source (AD or OpenLDAP). If you don't have any of that you can create local users in the vCenter Single-Sign on.
Hello,
i have the same problem. Do you have a solution?
Thank you.
How can this be done via CLI? I am trying to automate the post configuration of vCenter, adding AD authentication and then adding ad users/groups to the global permissions.
Hi
If you are still wondering: use the sso-add-native-ad-idp script that's in C:\Program files\vmware somewhere (search for it).
Pingback: vSphere-6:Part 5-Adding AD Authentication in vCenter Server | Go Virtual.
add identy source error
The "Add identity source" operation failed for the entity with the following error message.
Either the supplied name or alias is already associated with another domain, or an identity source with same name already exists.
It's November 2017 and I just wanted to let you know your work writing this article is still helping people! Thanks for taking the time to make this information available to everyone in the community