When you've installed the vSphere Management Assistant 6.0 (vMA) you very like came across its very strict password policy. With this requirements, the password recovery for vMAs is a common tasks. This post explains how to recover forgotten vMA passwords and how to use insecure, simple passwords for lab uses.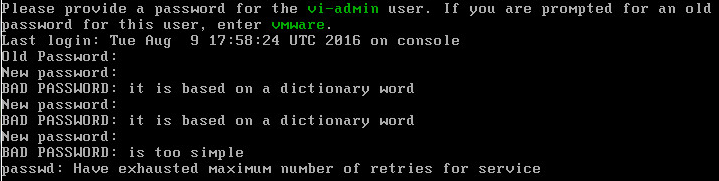
Please provide a password for the vi-admin user.
BAD PASSWORD: to short
BAD PASSWORD: it is based on a dictionary word
BAD PASSWORD: is too simple
...Have exhausted maximum number of retries for service
vMA vi-admin Password Recovery
The vSphere Management Assistant appliance has a very strict password policy so it might happen that you need to reset the password because you can't remember it. VMware has even made the single user mode password protected so the default Linux method of resetting passwords does not work.
Nevertheless, this is how you can reset the password for root, vi-admin, vi-user or any other user without using a live CD:
- Open the VM Console and reboot the vMA
- When the GRUB bootloader shows up, quickly press e. (You only have 7 seconds)
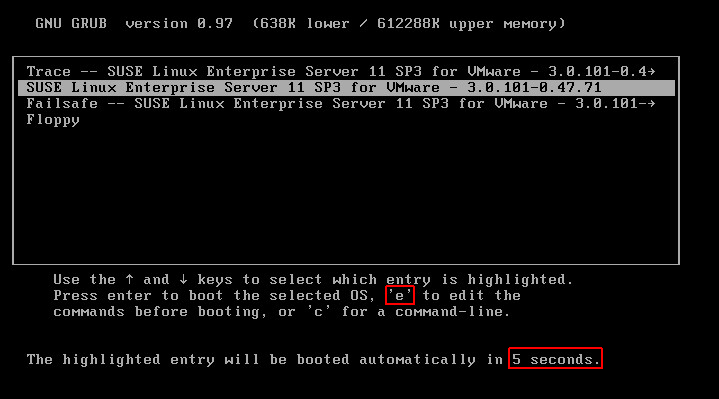
- Highlight the kernel line in the next screen and press e again.
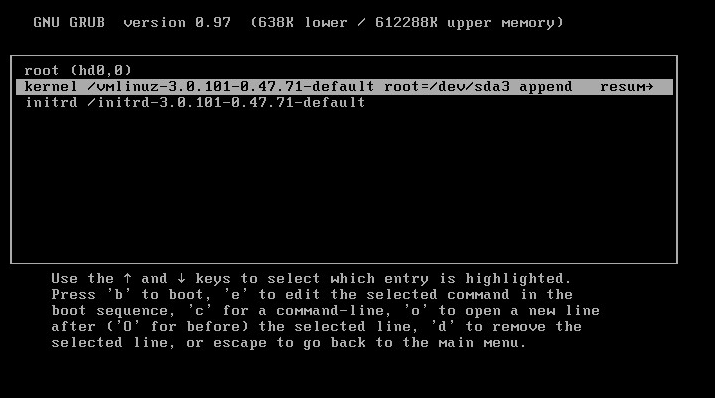
- Append init=/bin/bash in the kernel line and press enter.
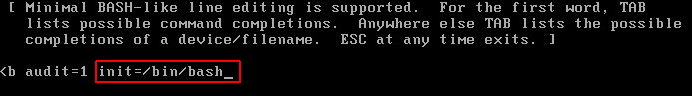
- Press b to boot
- The vMA should now boot and present a red prompt. Use passwd vi-admin to set a new password for the vi-admin user. You don't need to comply with any password policies except the password history.
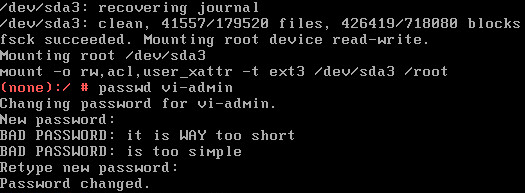
- Reboot or reset the VM
You should now be able to login with the new password.
Remove Password Security
For demos and labs there might be the requirement to use simple passwords and remove policies. The following section explains how to disable security features used with the vMA. All security changes require root permissions. The vi-admin user can elevate to root with the command "sudo -s".
Needless to say that you should not use that in production.
Bypass Password Complexity
Password and authentication policies are defined in /etc/pam.d/ with the following settings preconfigured by VMware:
- pam_cracklib.so dcredit=-1 ucredit=-1 lcredit=-1 ocredit=-1 minlen=8 difok=4 retry=3
- pam_pwhistory.so enforce_for_root remember=5 retry=3
- pam_tally2.so deny=3 onerr=fail even_deny_root unlock_time=86400 root_unlock_time=300
This sets the password policy to the following requirements:
- dcredit=-1 -> Password requires 1 lower-case characters
- ucredit=-1 -> Password requires 1 upper-case characters
- lcredit=-1 -> Password requires 1 numeric characters
- ocredit=-1 -> Password requires 1 special characters
- minlen=8 -> Password requires at least 8 characters
- difok=4 -> 4 Characters must be different from the previous password
- retry=3 -> You have 3 attempts to pick a good password before the passwd program aborts
- remember=5 -> The last 5 passwords can not be used
- deny=3 -> Account is logged after 3 failed login attempts
- unlock_time=86400 -> Unlock time for users: 1 day
- root_unlock_time=300 -> Unlock time for root: 5 minutes
Reset to SLES defaults:
rm /etc/pam.d/common-password ln -s /etc/pam.d/common-password-pc /etc/pam.d/common-password rm /etc/pam.d/common-auth ln -s /etc/pam.d/common-auth-pc /etc/pam.d/common-auth chmod +x /usr/sbin/pam-config pam-config -d --cracklib pam-config -d --pwhistory
Some basic requirements are still active and can only bypassed by the root user.
Unlock User after 3 failed login attempts
When a user enters the wrong password 3 times, the account is locked for 1 day. Check failed login attempts:
# pam_tally2 --user vi-admin Login Failures Latest failure From vi-admin 10 08/09/16 19:09:14 172.16.0.31
Reset the counter and unlock the account:
# pam_tally2 -u vi-admin --reset
Enable Single-User Mode without root password
As explained above, it is required to enter the root password when booting into Single-User Mode.
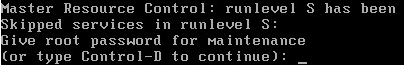
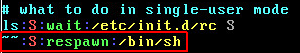
To remove the password prompt for single-user mode edit /etc/inittab and change...
~~:S:respawn:/sbin/sulogin
to...
~~:S:respawn:/bin/sh