The vCenter Server has an internal user database that allows you to add and manage users with the vSphere Web Client. Users management and Single Sign-On is provided by the Platform Service Controller which is available since vSphere 6.0. In a large environment, you might want to connect your virtualization infrastructure to a centrally manage Active Directory.
This article explains how to add AD authentication in vSphere 6.5 and how to get the "Use Windows session authentication" checkbox to work with the enhanced authentication plugin. This works for both, the vCenter Server 6.5 installed on a Windows Server and the vCenter Server Appliance (vCSA).
- Open vSphere Web Client (https://[vcenter]/vsphere-client)
- Login as Single Sign-On Administrator (Password set during installation)
- Navigate to Administration > Single Sign-On > Configuration
- Open the Identity Sources tab
- Click the green + to add an identity source
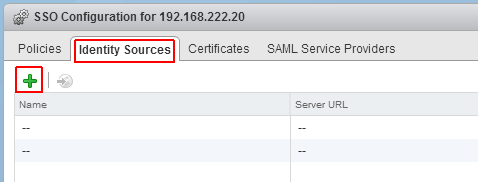
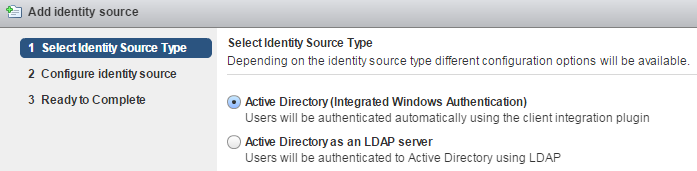
- Select Identity Source Type:
A) Active Directory (Integrated Windows Authentication)
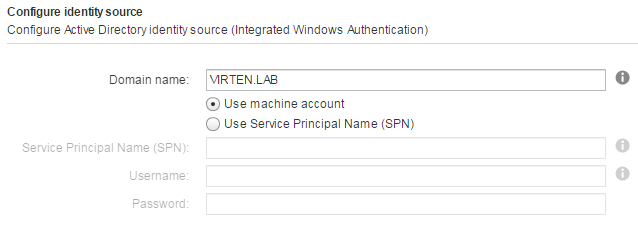
This option works with both, the Windows-based vCenter Server and the vCenter Server Appliance. The underlying system has to be a member of the Active Directory domain. (To join the vCSA to an AD, read this post.)
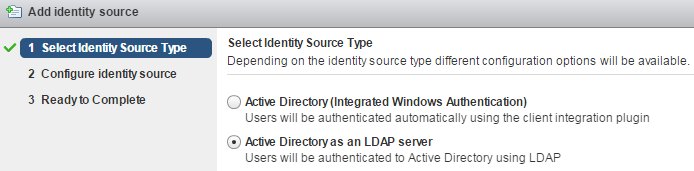
 B) Active Directory as a LDAP Server
B) Active Directory as a LDAP Server
If the underlying system is not part of the Active Directory domain.
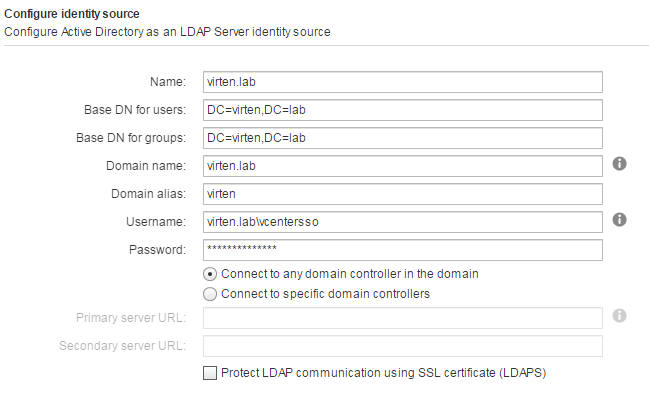
 Fill out the remaining fields as follows:Name: Label for identification
Fill out the remaining fields as follows:Name: Label for identification
Base DN for users: The Distinguished Name (DN) of the starting point for directory server searches. Example: If your domain name is virten.lab the DN for the entire directory is "DC=virten,DC=lab".
Base DN for groups: The Distinguished Name (DN) of the starting point for directory server searches.
Domain name: Your domain name. Example: "virten.lab"
Domain alias: Your NetBIOS name. Example: "virten"
Username: A user in the AD Domain with at least browse privileges. Example virten\vcenterssoSelect "Connect to any domain controller in the domain" of you want to use DNS to identify domain controllers or configure static primary and secondary URLs. When using static entries, you can either query the local directory (Port 389), or the global catalog (Port 3268).
Example: "ldap://dc01.virten.lab:3268"
- Click Next and finish the configuration wizard
- Back at Identity Sources your AD should appear in the list and from now on you are able to assign vCenter permissions to users and groups from your active directory.
- Select you Active Directory and click the world with arrow button to make AD to your default domain.
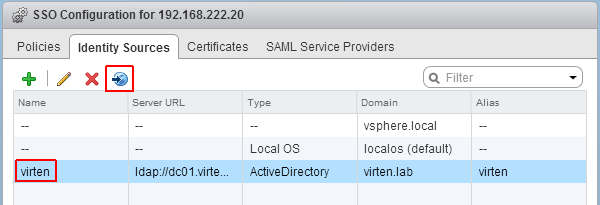
- To login with AD users, you have to set permissions. To add a AD user as global Administrator navigate to Administration > Access Control > Global Permissions
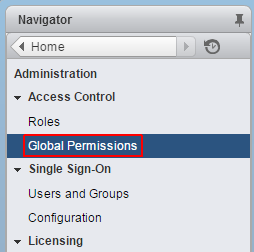
- Click Add permission
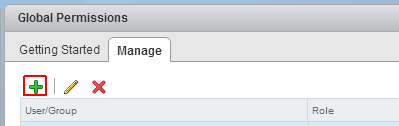
- Click Add...
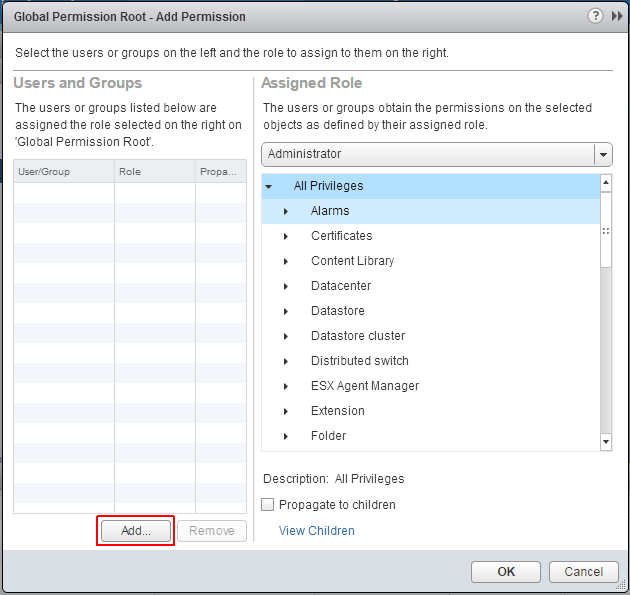
- Select the Active Directory domain under Domain, choose a user and press Add
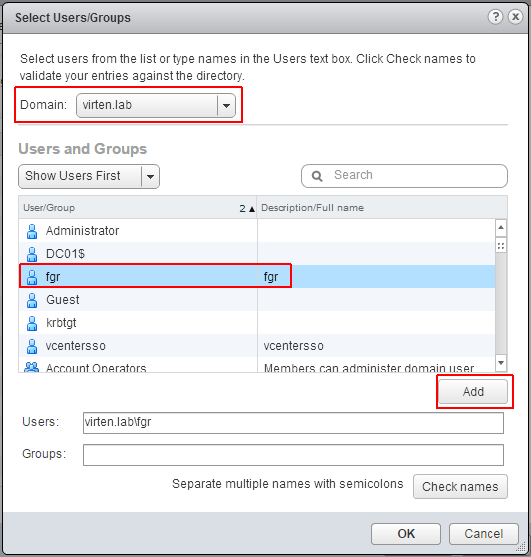
- Press OK twice
You should now be able to login to the vCenter 6.5 with your Active Directory account.
Use Windows session authentication
The "Use Windows session authentication" checkbox is disabled unless the Enhanced Authentication Plugin is installed. You can find the download link at the bottom of the login screen.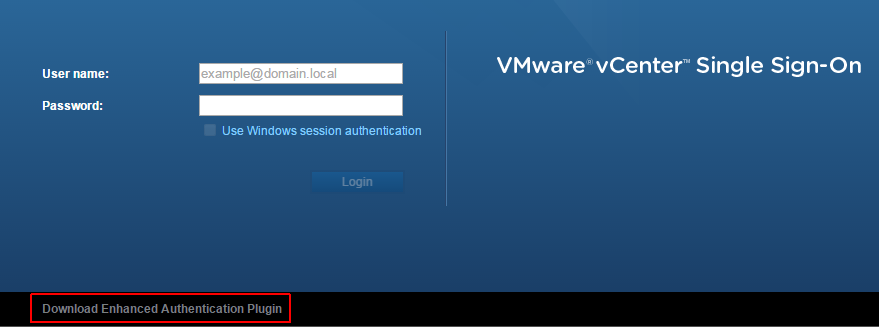
The vCenter Single Sign-On server is not currently joined to any domain.
When the following message is displayed:
The vCenter Single Sign-On server is not currently joined to any domain. You cannot complete the current operation.
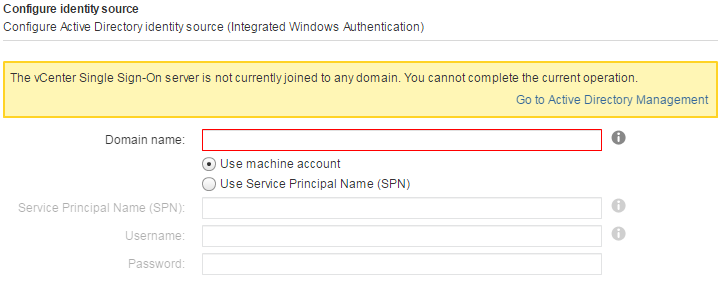
Join the underlying operating system to an Active Directory domain or use this guide to add the vCenter Server Appliance is an AD.
Great post there. Many thanks.
Hi fgrehl
great post as usual!
Just a question about
Active Directory (Integrated Windows Authentication) and Active Directory as a LDAP Server?
What is the suggested method? What do you usually do in a production environment and why?
Greetings, in vSphere 6.5, Global Permissions for Administrators who need to view VMware Licenses. Can you explain this in more detail, currently on the administrator@vsphere.local account can view the licenses. The above account is in the vCenter Administrators group, if you add a new account to this group you still cannot view the licenses. This configuration is NEW in vSphere 6.5.
This was a reference link I found for vSphere 6.0 which works fine however in vSphere 6.5 it is not working. https://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2120255
Hi,
did someone try to use a ldaps Server already with a root-certification??
Till 6.0U2a it was working, BUT vsphere 6.5 is not able to handle this, SR by VMware is open since End November 2016 );-(.
Thank you. Hoped that VMware documentation would have explained it like this.
Integrated would be used if the vCenter server has been joined to the domain. In a production environment, you may connect to many domains if you have customers from many different orginizations all with their systems installed so it would depend on your situation
Excellent, very helpful, thanks!
Does someone test the integrated or ldap mode with a trusted (two way - single forrest)domain? I want to use the login with Windows session credentials from Domain B, but it does not work.Login with username / Password works but not with the eap plugin. Any suggestions?
great work, please keep it up.
thanks saif
Hi fgrehl ,perfect instructions, they work with AD 2008 R2 and Active Directory as an LDAP Server. In September we will have to migrate to Active Directory 2016. I read this https://kb.vmware.com/s/article/2071592, it seems that VCSA 6.5 and 6.7 are not compatible with AD 2016. I have 6.5. What this mean? The AD users can not login to the VCSA? Do you know anything about it?
Hi Michele, we are running vSphere 6.5 U2 and AD 2016 without any problems. Didn´t even know that there is a KB for this ;)
Faced with the same issue. Our AD Team is trying to upgrade now and is hammering me for answers in this. I can’t beleuve VMware is not in this already... they should have stayed out of the SSO business entirely their implementation sucks and has been nothing
But headaches since 5.1... now they have to keep developing it.. I would rather see development of the thick client over PSC/SSO.. my 2 cents.
helped me.
thankx.
How would I install the vCenter client I ahave the SSO but I am unable to install the client
Has anyone figured out how to add an integrated windows authentication identity source via script in 6.7? In 6.0 we used the sso-add-native-ad-idp.sh script, but that no longer exists.
Is this site aware? Does "connect to any domain controller in the domain" check only the local site? Or does it randomly pick any DC in the domain (even the ones in China when you are in the UK - see the problem?)