If you are working with Linux you are very likely familiar with SSH Keys. Public Key authentication is an authentication method that relies on a generated public/private keypair and enables a secure method to login without entering a password.
Usually, you would use ssh_copy_id to transfer keys to a remote system or add it to the authorized_keys file manually but NSX-T does not support those methods. This article explains how to enable ssh key authentication for NSX-T Managers and Edge Appliances.
This article assumes that you already own an SSH keypair. If you are new to SSH keys, see this article which also explains how to create a key with Windows.
Connect to the NSX-T Manager with SSH and login as admin
The command syntax to add keys is:
set user [USER] ssh-keys label [LABEL] type [TYPE] value [PUBLIC KEY]
A typical authorized_keys entry is in the format TYPE KEY LABEL.
Example: ssh-rsa AAAAB3NzaC1yc2EA[...] FGrehl
- Label: FGrehl
- Type: ssh-rsa
- Public Key: AAAAB3NzaC1yc2EA[...] (Very long string)
The command should look like this:
# set user admin ssh-keys label FGrehl type ssh-rsa value AAAAB3NzaC1yc2EAAAABJQAAAQEAkLay97hBPztwqsvMVlMWXRHqm9n5NIn6mWON1kxkTdqC+NrpVgBnmCdgQy20DD8OViByYY+kzGCDR9N0aaiJ9DK0Irkw7Siv/BMzf5r7vAVeqbUrfeTCOxB71pfvqEoco1q39TPAXiMx4CNppiUvx1mZbd/EGcChpzcsSDipaudRthosmGYTqa/3RsaUHVFqHnbOP09LqNl+mdtuUAedLSBG/B4Db4mzZZlGul05WaRcJRyTzry+xCMc52OeoieNsqGkzKJFi58AzHfTKo/wonhKR/UGQPsSkhUTZhec3vRpfsOHIr4riRpkOBFmSjmm4if0vkPdzlvgVHyLZACxOQ==
When adding keys for root and admin, you have to enter the user's password.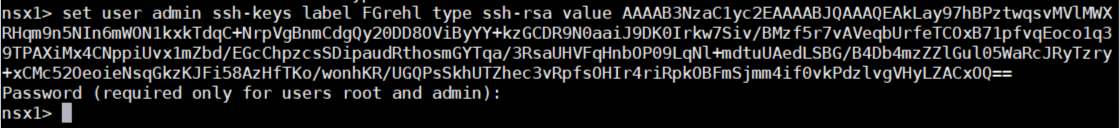
If you want to add multiple keys for a single user (which is common practice), just use different labels. By using the key owners name as label you can later identify to whom the key belongs.
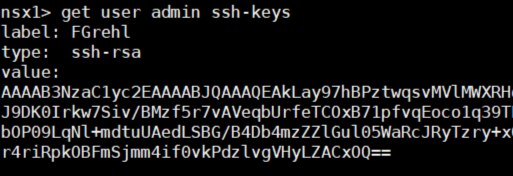
Use get user admin ssh-keys to verify keys.
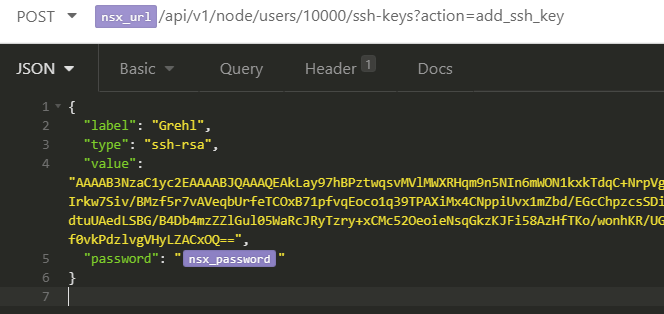
You can also add keys by using the NSX-T API, with a simple POST request. The following request adds a key for the admin user (Userid 10000):
POST https://<nsx-mgr>/api/v1/node/users/10000/ssh-keys?action=add_ssh_key
{
"label": "FGrehl",
"type": "ssh-rsa",
"value": "AAAAB3NzaC1yc2EAAAABJQAAAQEAkLay97hBPztwqsvMVlMWXRHqm9n5NIn6mWON1kxkTdqC+NrpVgBnmCdgQy20DD8OViByYY+kzGCDR9N0aaiJ9DK0Irkw7Siv/BMzf5r7vAVeqbUrfeTCOxB71pfvqEoco1q39TPAXiMx4CNppiUvx1mZbd/EGcChpzcsSDipaudRthosmGYTqa/3RsaUHVFqHnbOP09LqNl+mdtuUAedLSBG/B4Db4mzZZlGul05WaRcJRyTzry+xCMc52OeoieNsqGkzKJFi58AzHfTKo/wonhKR/UGQPsSkhUTZhec3vRpfsOHIr4riRpkOBFmSjmm4if0vkPdzlvgVHyLZACxOQ==",
"password": "password"
}
Is there a way to persistent these key accross nsx updates? Every update we have to re-push our keys to every edge node >.>
You can automate deployment with Ansible for example:
https://www.virten.net/2021/03/deploy-nsx-t-edge-vm-ssh-keys-with-ansible/
thanks this helps at least to deploy the keys quickly again
especially with the `-k, --ask-pass` ansible-playbook option :)