NSX-T 3.0 has added support for authentication using AD or LDAP sources. In previous versions, you had to deploy the vIDM (VMware Identity Manager) appliance to allow external authentication. You can still use vIDM but if you only need NSX-T authentication you can now do it without a sole purpose appliance.
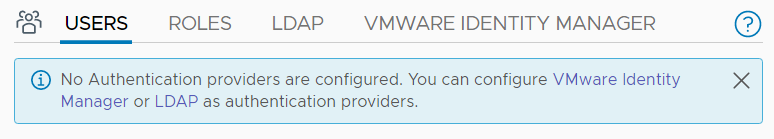
This article explains how to enable LDAP authentication in NSX-T 3.0.
Add LDAP Identity Source in NSX-T 3.0
- Open NSX-T Manager GUI
- Navigate to System > Settings > Users and Roles
- Open the LDAP Tab and click Add Identify Source
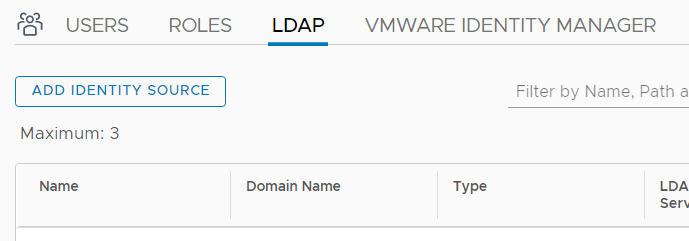
- Fill out the fields:Name: A label for the identity source
Domain Name: Your domain name. Example: "virten.lab"
Type: Specify LDAP Type (AD or OpenLDAP)
Base DN: The Distinguished Name (DN) of the starting point for directory server searches. Example: If your domain name is virten.lab the DN for the entire directory is "DC=virten,DC=lab".
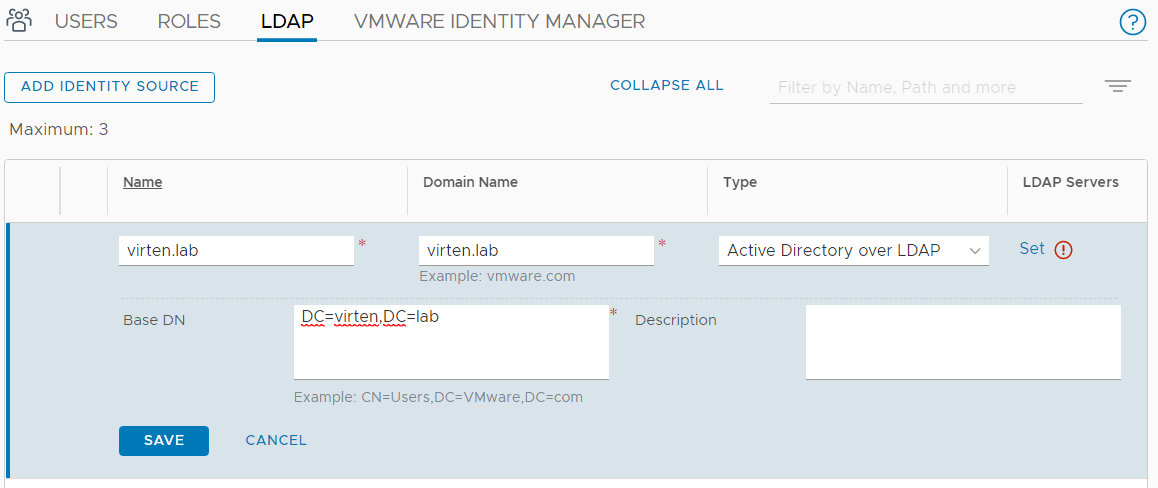
- Click Set (next to LDAP Servers)
- Click Add LDAP Server
- Enter LDAP Server Information and press Check Status
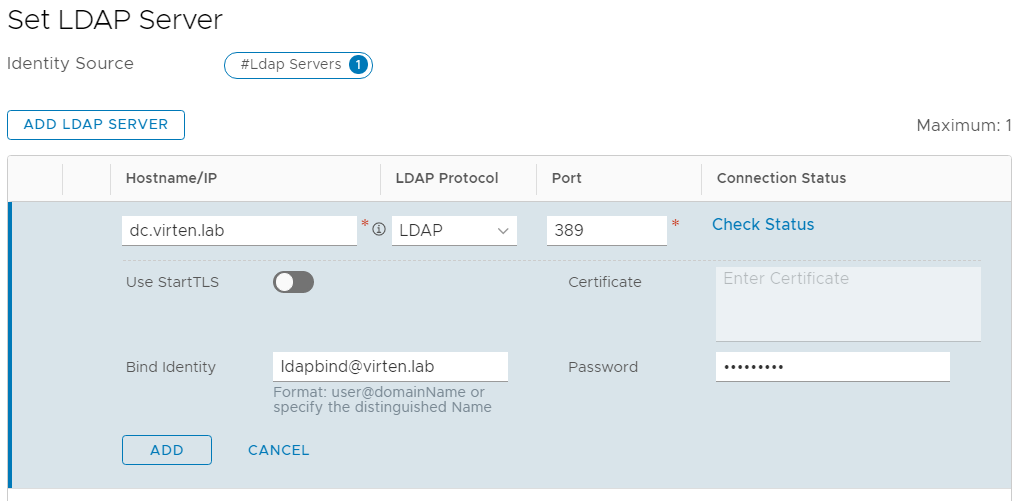
- When the connection is successful, press ADD followed by APPLY.

- Press SAVE to finish the Identity Source configuration.
You should now have successfully added an LDAP Identity Source. To log in with LDAP users, you have to create User/Group to Role mappings.
Create User/Group to NSX-T Role Mappings
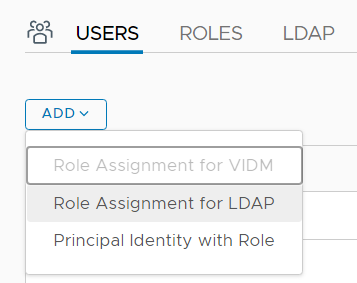
- Open the USERS Tab in System > Settings > Users and Roles
- Click ADD > Role Assignment for LDAP
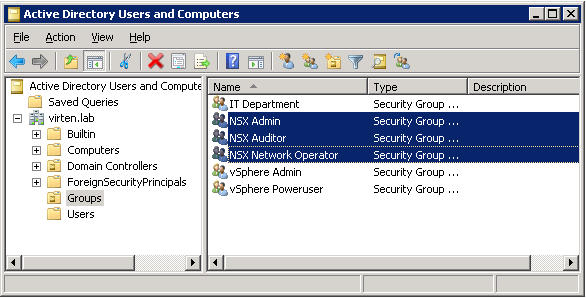
- I've prepared 3 AD Groups: NSX Admin, NSX Audit, and NSX Network Operator.
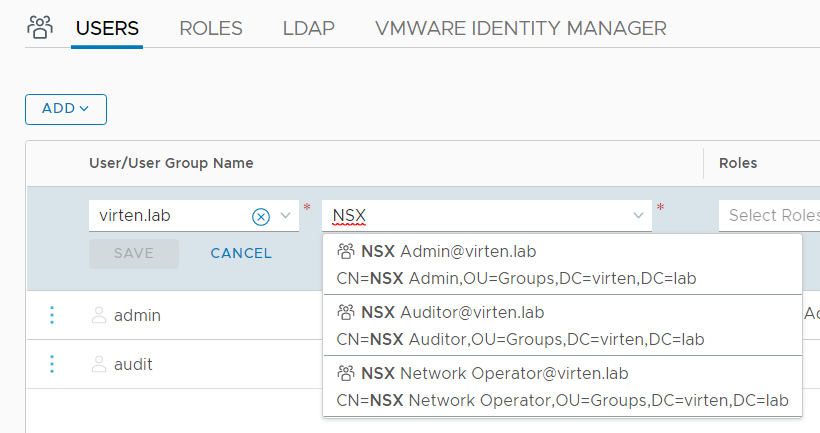
- Select your Domain and start typing to search AD users or groups.
- Choose a Role (Enterprise Admin is the highest role in NSX-T)
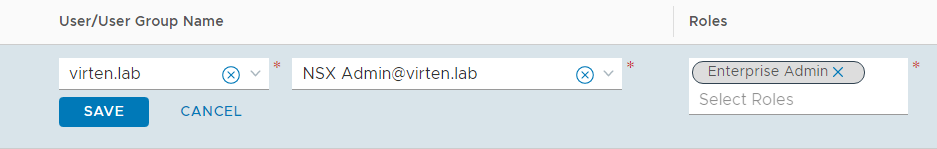
- Add additional role mappings according to your requirements. If you want to know which permissions each role has, check the Roles tab. You cannot add any new roles at the moment.
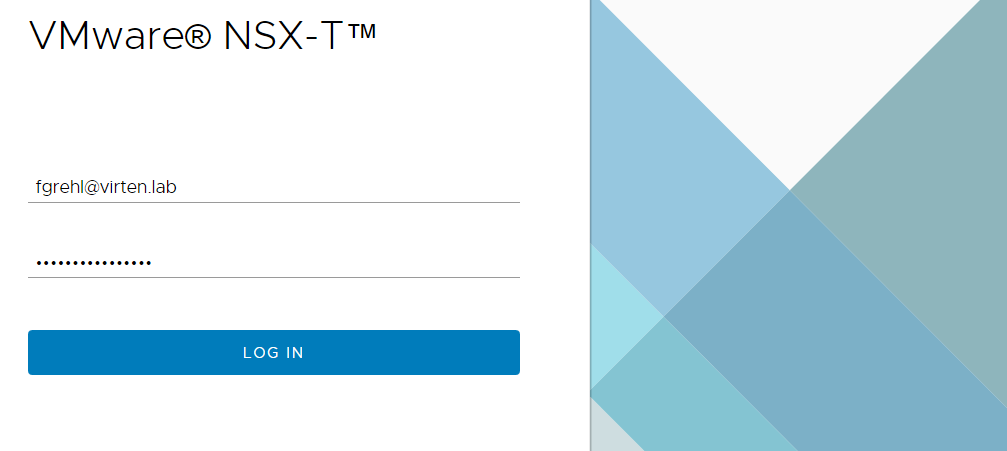
You can now login with your LDAP user.
Unfortunately there is no option to use more then one dc.:(
But it is a .0-relaese with room for improvement and this option is much more better the vidm.
Can't you add 3 Domains (Identity Sources), but only 1 LDAP Server per Domain?
Hey. I configured this Option in our lab environment. It works, but sometimes the ldap connection is down when you chose System | Users and Roles | USERS.
Error: "LDAP Server Connection is down for 1 Identity Source. View configuration"
So the service sometimes looses the connection to the ldap server. Waiting a while and reloading the site mostly helps. In this state you also can't define ldap-users. Alternatively you can hit "check status" in the ldap server settings several times until it is again "successful".
Anyone here with same or similar effects after implementing ldap auth?
Thanks in advance für your advice!
using 3.1.1 my ldap server connects but the identity source fails have you any ideas? thanks
Hi, in NSX-T 3.2.0 now you can configure more than one LDAP-Server for the same directory.
I want to do this by API calls (or ansible).
But it seems there are only API calls for managing existing LDAP sources, but none for creating a new one...
Any idea?