On August 8th, 2023, intel disclosed a transient execution side-channel vulnerability impacting Intel processors. Information exposure through microarchitectural state after transient execution in certain vector execution units for some Intel Processors may allow an authenticated user to potentially enable information disclosure via local access.
Additional Information
- Intel Security Advisory: INTEL-SA-00828
- CVEID: CVE-2022-40982
- Affected CPU Table
- VMware Statement ("ESXi may be impacted")
- Vendor Information: HP
- Vendor Information: Dell
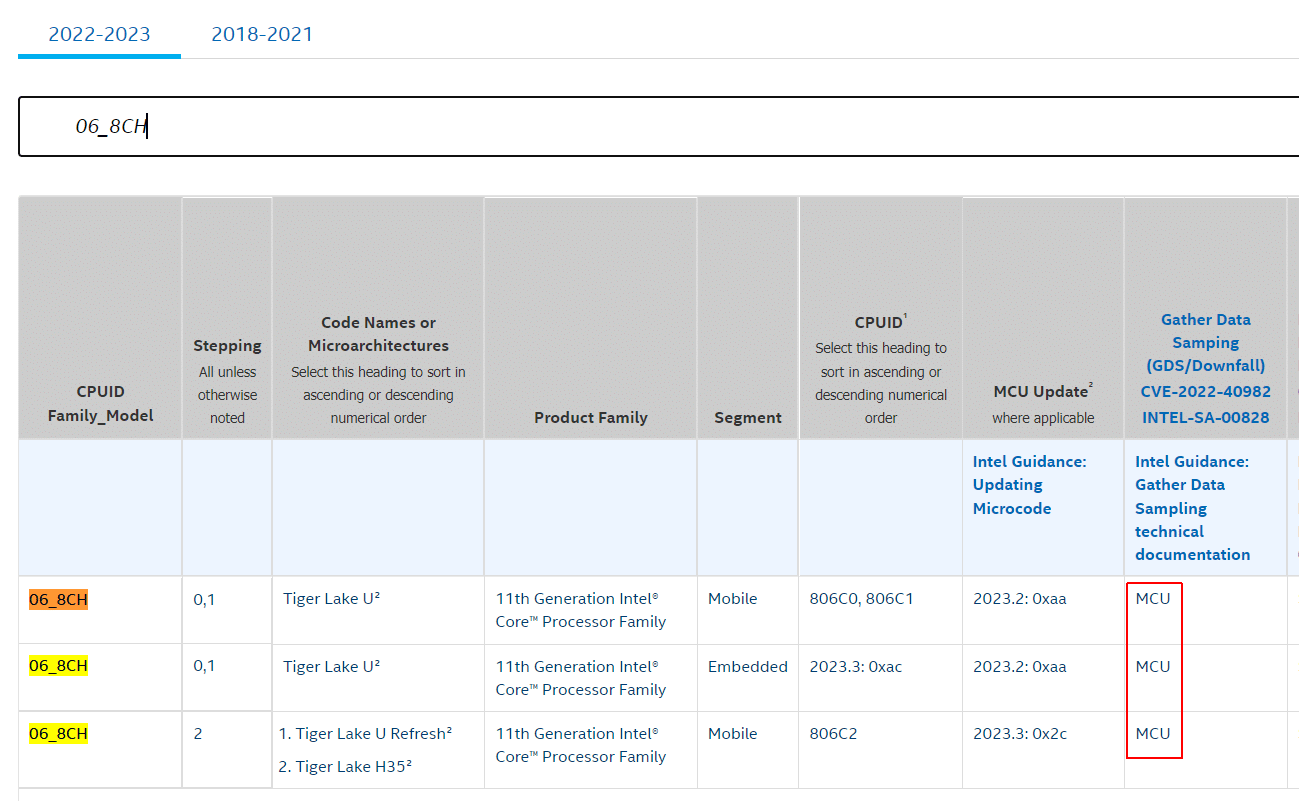
To identify your CPU in Intels Affected CPU Table you need CPU Family, Model, and Stepping, which can be gathered programmatically using PowerShell:
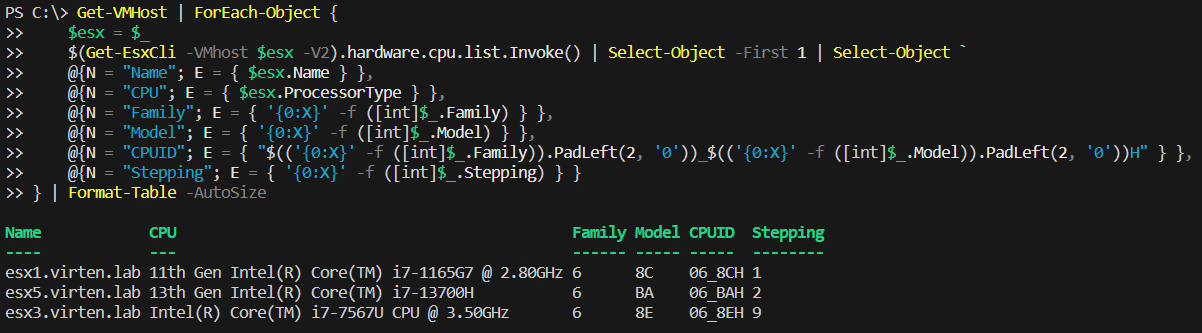
The script is available here: get-cpuid.ps1
Use CPUID to identify the CPU type and check the GDS column. If it states "MCU", a microcode update is required for mitigation. Check with your Hardware Vendor to receive the upgrade.