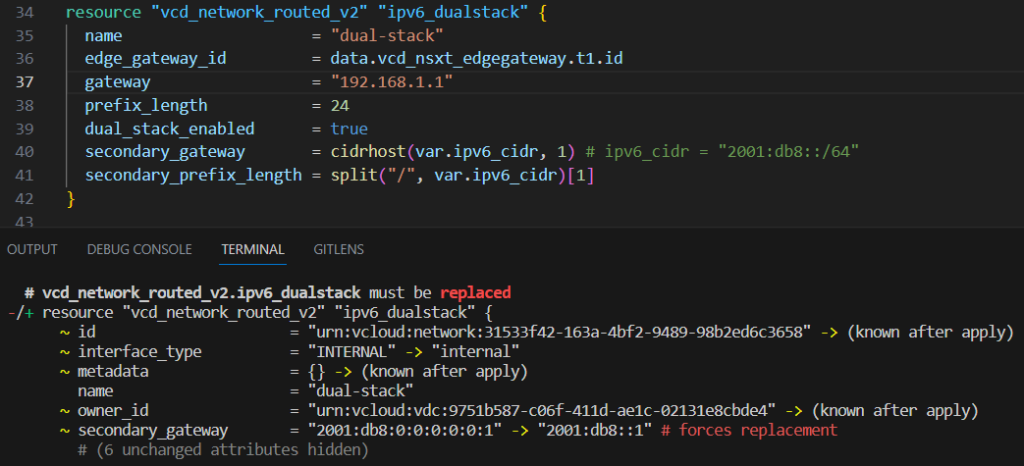
Deploy High Available Firewall Appliances in VMware Cloud Director
When customers are deploying their services to a Cloud Datacenter delivered with VMware Cloud Director they quite often want to use their own virtual Firewall Appliance rather than the Edge and Distributed firewall that is built into the NSX infrastructure. Many Administrators prefer to use their well-known CheckPoint, Fortinet, or pfSense for seamless configuration management. While using standalone virtual Firewall Appliances is not an issue in general, there are some caveats with HA deployments, which can be addressed with features implemented in recent versions of VMware Cloud Director.
This article explains how to deploy High-Available Firewall Appliances in VMware Cloud Director 10.5
Read More »Deploy High Available Firewall Appliances in VMware Cloud Director
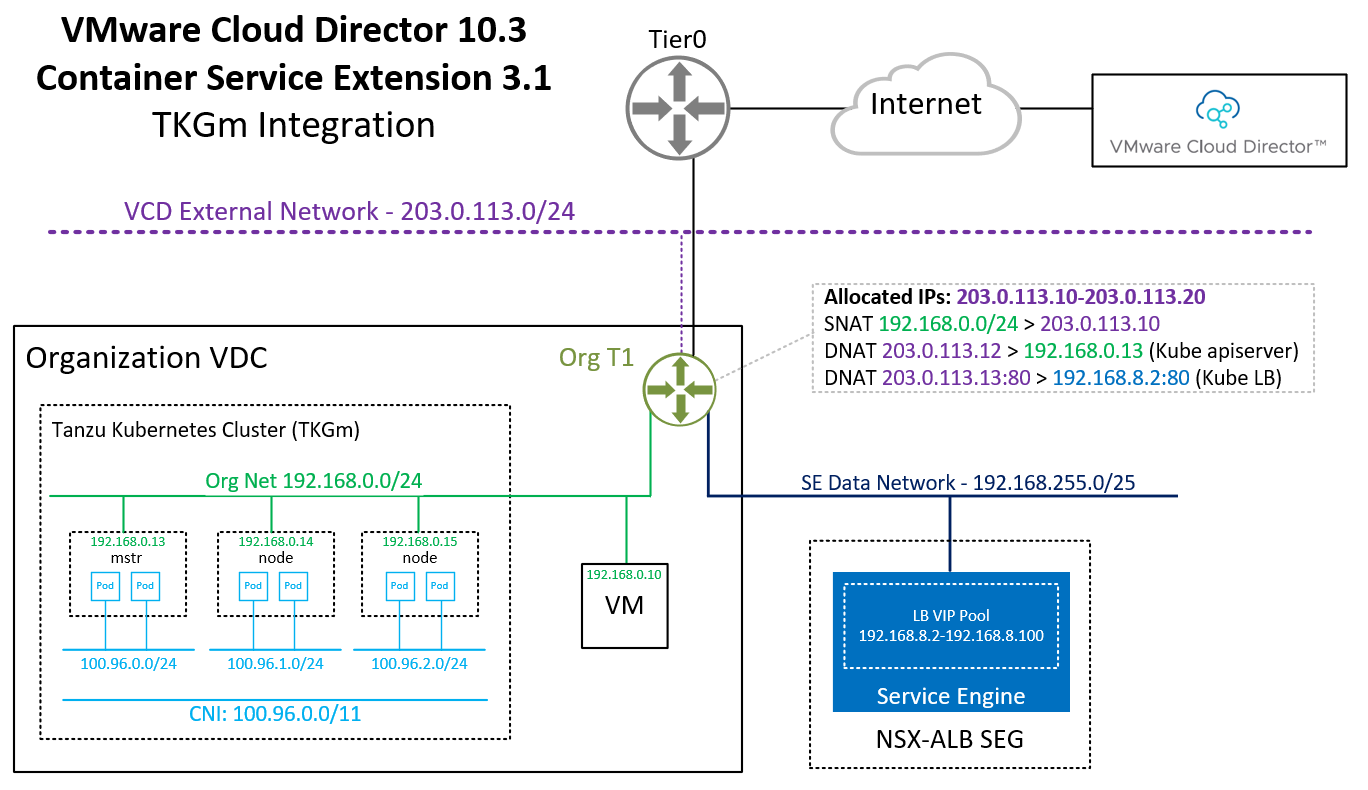
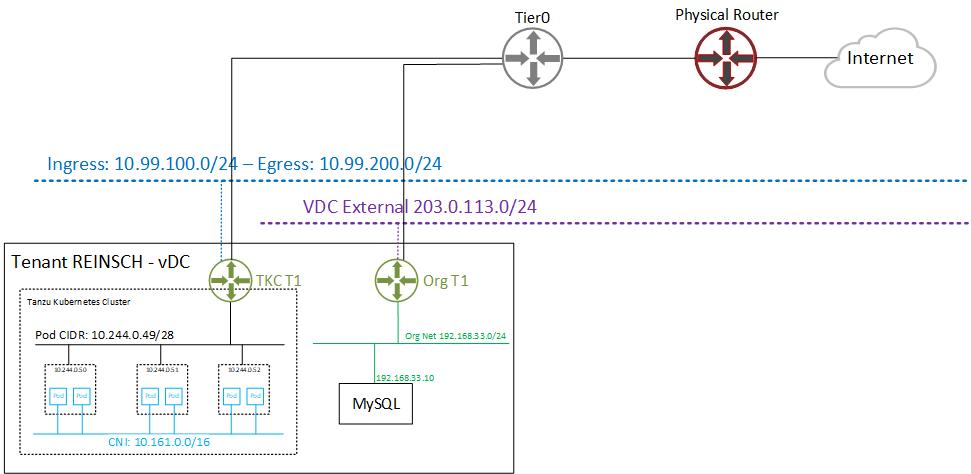
 This article recaps Issues that I had during the integration of VMware Container Service Extension 3.1 to allow the deployment of Tanzu Kubernetes Grid Clusters (TKGm) in VMware Cloud Director 10.3.
This article recaps Issues that I had during the integration of VMware Container Service Extension 3.1 to allow the deployment of Tanzu Kubernetes Grid Clusters (TKGm) in VMware Cloud Director 10.3.